IPsec or (IP Security). IPsec is a convention suite that encodes the whole IP activity before the bundles are exchanged from a source to a destination. IPsec is additionally able and in charge of verifying the two nodes before the real correspondence happens between them. IPsec can be arranged to utilize any of the accessible calculations to encode and decode the system activity.
IPsec can be arranged to work in both of the two accessible modes:
Transport Mode – In This Mode, IPsec just scrambles and/or verifies the real payload of the parcel, and the header data stays in place.
Tunnel Mode – In This One, IPsec scrambles and/or verifies the whole bundle. After encryption, the parcel is then epitomized to frame another IP bundle that has diverse header data. IPsec is designed to be utilized as a part of Tunnel Mode while making secure site-to-site Tunnel VPN.
While A VPN (Virtual Private Network) is a kind of system setup in which the general population telecom medium and general society system, i.e. the Internet, is utilized to transmit information from one office at one land area to another office at another geological area. Since general society telecom medium and general society system is inconsistent concerning security of the data, overseers make secure passages between the source and destination locales. The information is exchanged by means of these passages.
Since the passages that overseers make just permit correspondence between the source and destination hubs/destinations, the clients can get to the information and assets from the remote areas as basically and effectively as though they were getting to the data in through their locals.
Finally a SITE As far as concerned with PC systems administration and VPN, a site is a range or premises of an office in which two nodes that are associated with one another can convey over high transfer speed system medium for instance 1 Gbps, 2Gbps or above. Hypothetically, if two nodes are joined with one another by means of any 10 Mbps or above transfer speed system (Bandwidth), they are thought to be on the same system site.
Associations that have numerous branches scattered over the world by and large utilize VPNs to interface one branch office to another, or to empower correspondence between the branch workplaces and the head office/datacenter.
So how this 3 mixes work together?
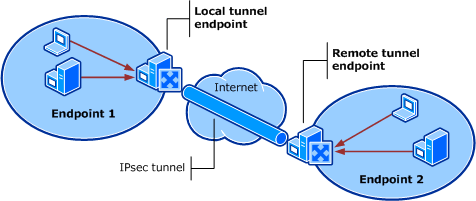
The following is the procedure that happens amid site-to-site correspondence more than an IPsec VPN site-to-site burrow:
The source PC PC1 advances the parcel Parcel1 with the destination IP location of the other PC PC2 to the router Router1 (default passage).
The Router1 gets the Parcel1 and encodes the whole bundle utilizing the predetermined calculation.
Subsequent to encoding the parcel, the Router1 epitomizes the entire bundle to frame another new parcel NewP1. This parcel has IP location of Router1 as source IP and the IP location of the Router2 (the switch put at the destination area) as the destination IP.
The Router1 then advances the bundle NewP1 to the IP location of R2 utilizing the Internet.
The destination switch Router2 gets the bundle.
The Router2 capsulates the NewP1 to get the first bundle Parcel1.
The Router2 unscrambles the Parcel1 utilizing the proper calculation.
The Router2 then advances the Parcel1 to the destination PC2, where the parcel was really expected to reach.
Preferences of Using IPsec VPN Site-to-Site Tunnels
IPsec VPN site-to-site passages offer various preferences. Some of them are:
- Necessity of purchasing devoted costly rent lines starting with one site then onto the next is totally disposed of as open telecom lines are utilized to transmit information.
- The inner IP locations of both the partaking systems and hubs stay escaped one another and from the outer clients.
- The whole correspondence between the source and destination destinations stays encoded which implies that risks of data robbery are amazingly low.
- Impediments of IPsec VPN Site-to-Site Tunnels.
A couple impediments of utilizing IPsec VPN site-to-site
- Costly switch is needed at every site to assume the part of the VPN server.
- Since embodiment, capsulation, encryption and unscrambling happen at the switches, these gadgets may face handling overhead and expanded CPU usage. In view of this, clients may experience diminished correspondence speed.
- The design procedure of IPsec VPN site-to-site is complex and obliges very gifted and qualified IT experts to be contracted to take care of business with flawlessness.